Overview
Expedient offers clients 2-factor authentication (2FA) to Expedient Secure User VPN with OneLogin as an identity provider. If preferred, a client can substitute OneLogin with alternative authentication options, including integrating an existing external solution like Active Directory. However, If a client chooses to use an alternative authentication option, it is the client's responsibility to manage that solution. While Expedient may not manage these alternative solutions, Expedient provides this documentation to assist clients with getting started on integrating their active directory with the Expedient Secure User VPN.
Prerequisites
The steps described in this document assume that the client has set up external authentication prerequisites and understands what protocol they should utilize to communicate with that service.
Process
Integrating an external authentication solution with the Expedient Secure User VPN, backed by Palo Alto Networks Global Protect, follows the same outline regardless of the solution.
Navigate to firewall UI after successfully authenticating into fw.expedient.cloud.
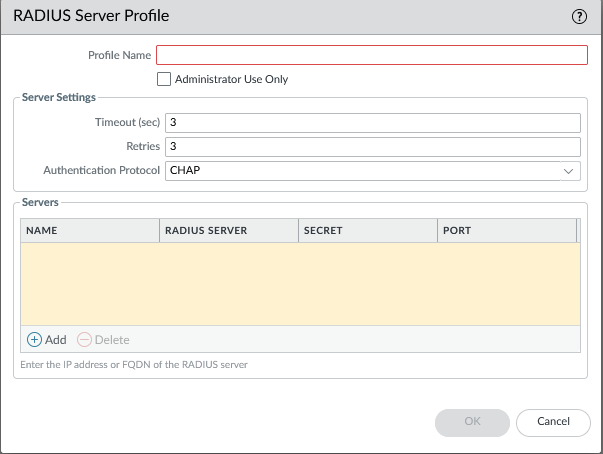
Create a server profile
Device > Server Profiles > select server type > +Add
In our example, we're utilizing RADIUS
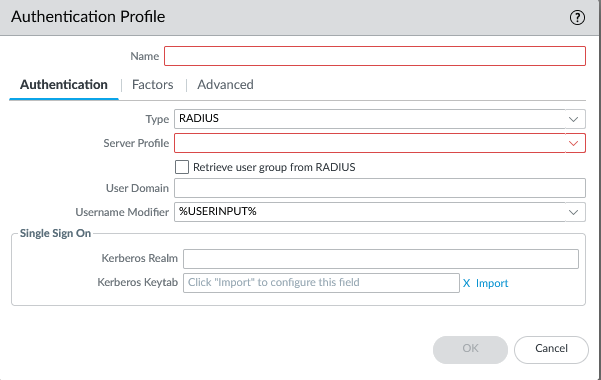
Create authentication profile utilizing server profile
Device > Authentication Profile > +Add
Access global protect portal & gateway configuration tabs and create client profiles pointing to the authentication profile.
Network > GlobalProtect > Portals > Select Portal > Authentication > Client Authentication > +Add
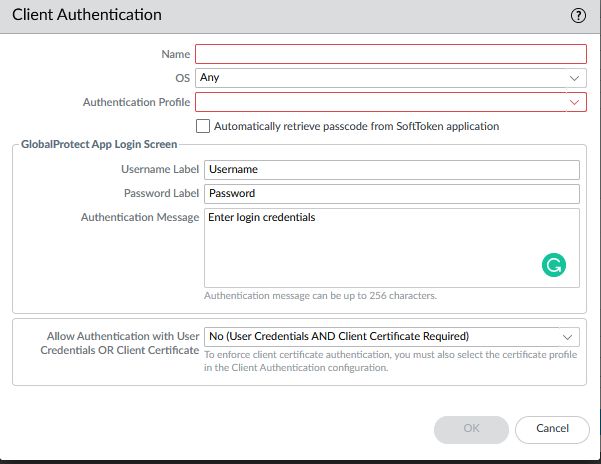
Network > GlobalProtect > Gateways > Select Gateway > Authentication > Client Authentication > +Add
Perform a firewall commit operation.
Please refer to the following Palo Alto Networks document for additional help configuring external authentication for Expedient Secure User VPN.
Configure External Authentication for Expedient Secure User VPN