This article will explain how to create a rule in Elastic Security to detect behavior associated with the Follina 0-day exploit, specifically to detect instances of the Microsoft Diagnostic Tool spawning from Microsoft Office processes. This rule will use EQL (Event Query Language) to search for evidence of this behavior in collected data.
- In Kibana, open the navigation sidebar and select Security > Alerts
- On the resulting page, select Rules from the sidebar
- At the top right of the page, click on Create new rule
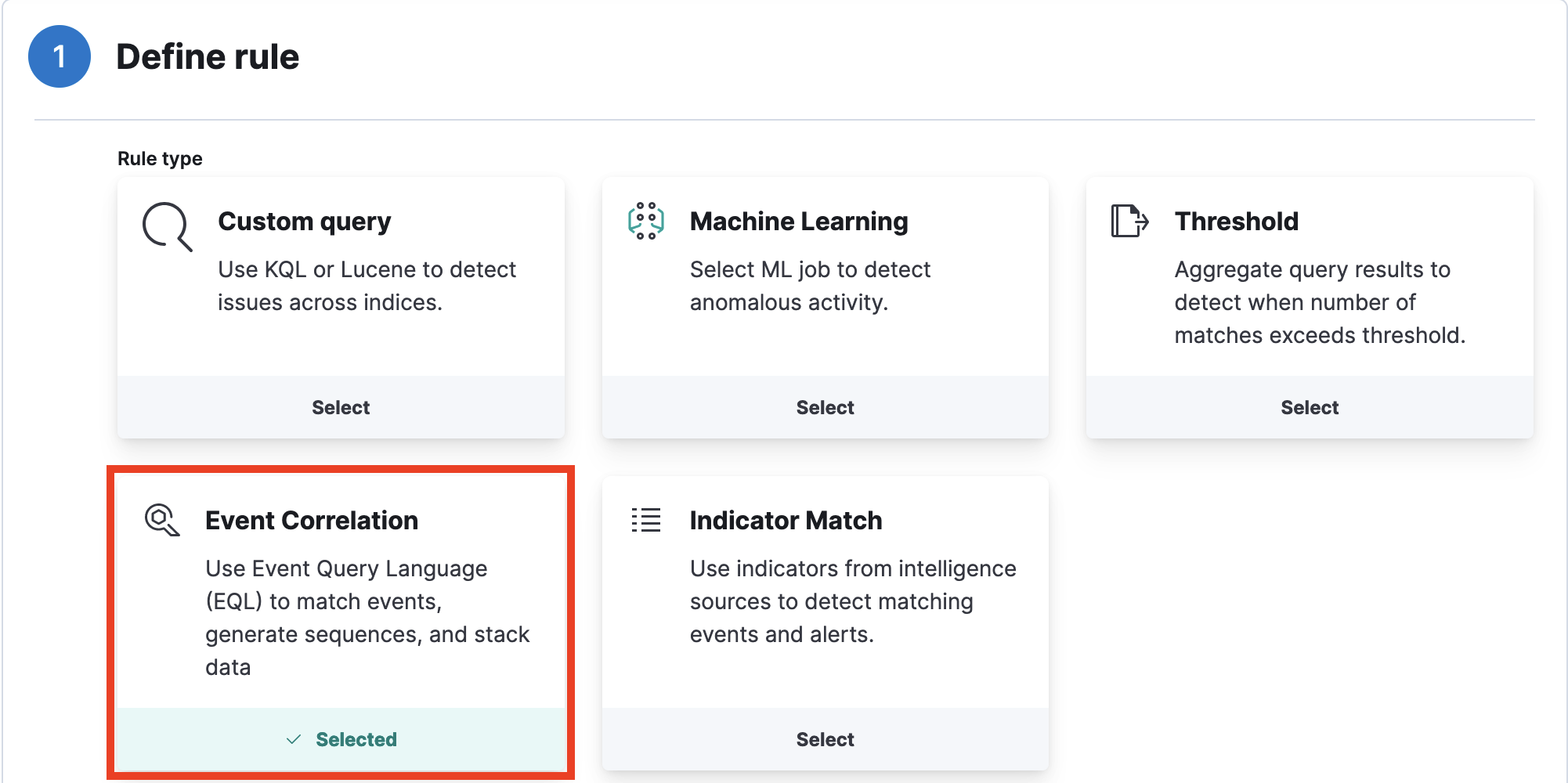
- This will bring you to the rule creation page. Start by selecting Event Correlation as the rule type
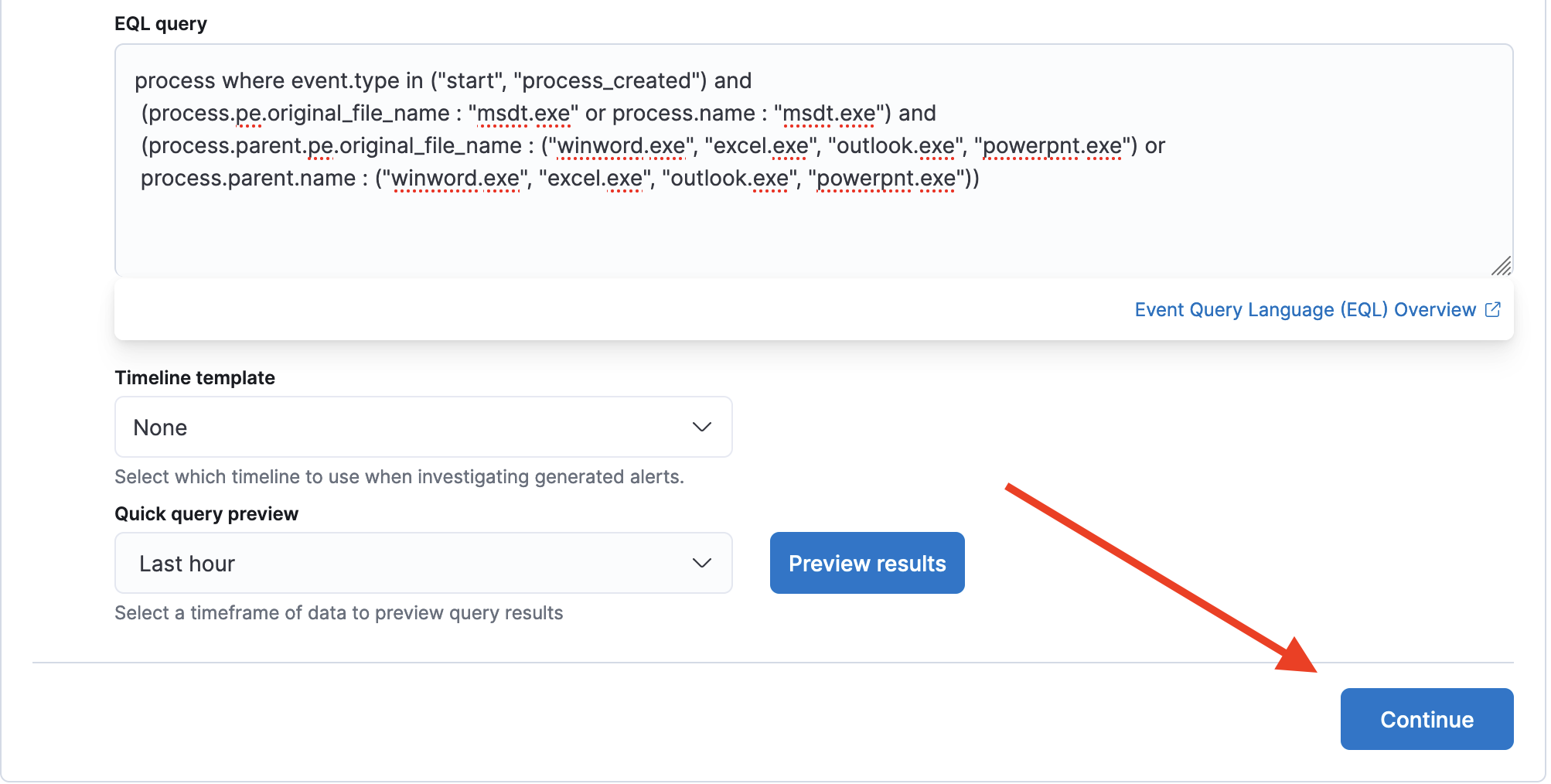
- Enter the following EQL query in the EQL query box that appears below and click continue:
process where event.type in ("start", "process_created") and
(process.pe.original_file_name : "msdt.exe" or process.name : "msdt.exe") and
(process.parent.pe.original_file_name : ("winword.exe", "excel.exe", "outlook.exe", "powerpnt.exe") or
process.parent.name : ("winword.exe", "excel.exe", "outlook.exe", "powerpnt.exe"))
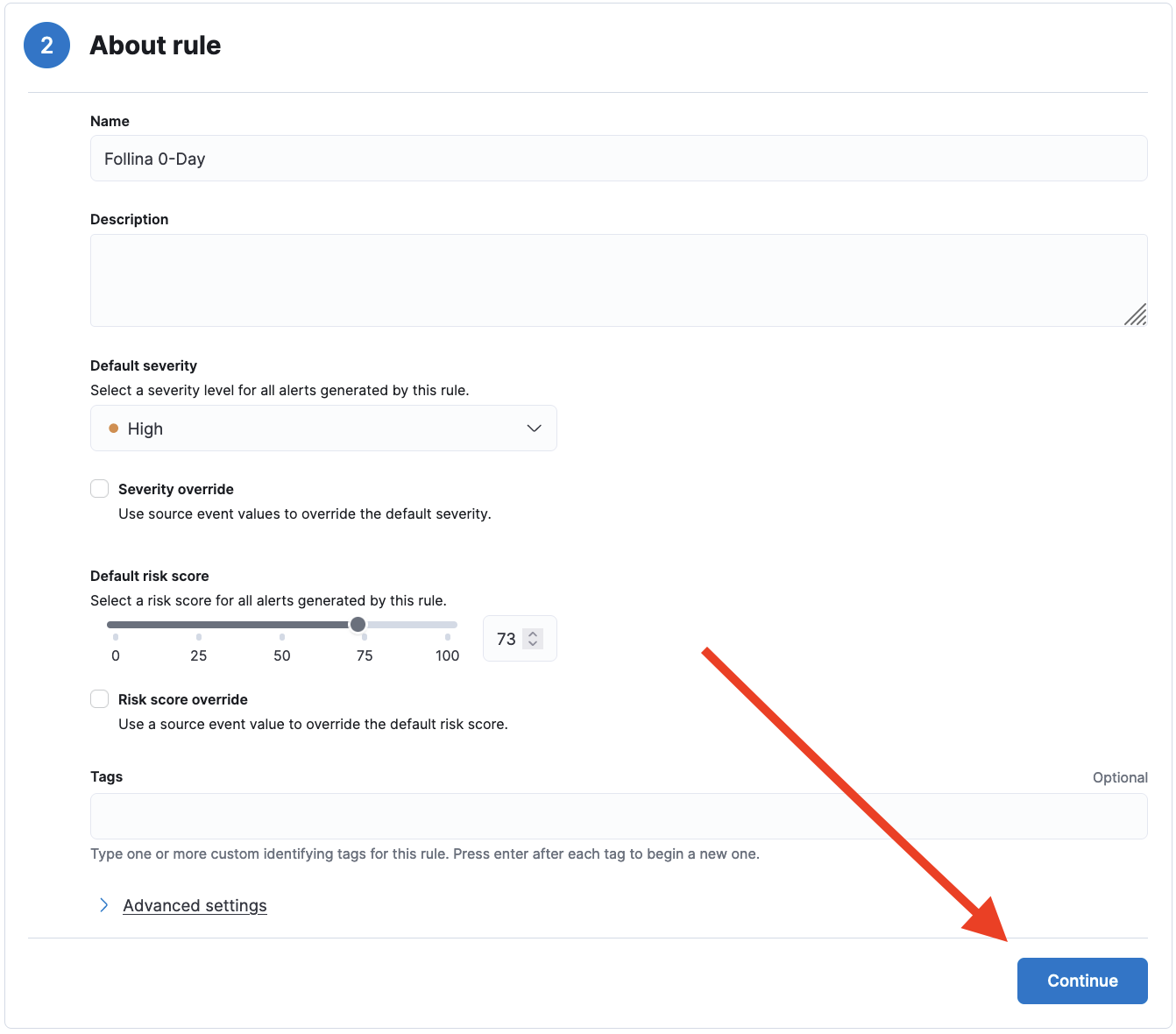
- In the next section, enter a Name, Description, and Default severity for the newly created rule as you see fit, and then click Continue
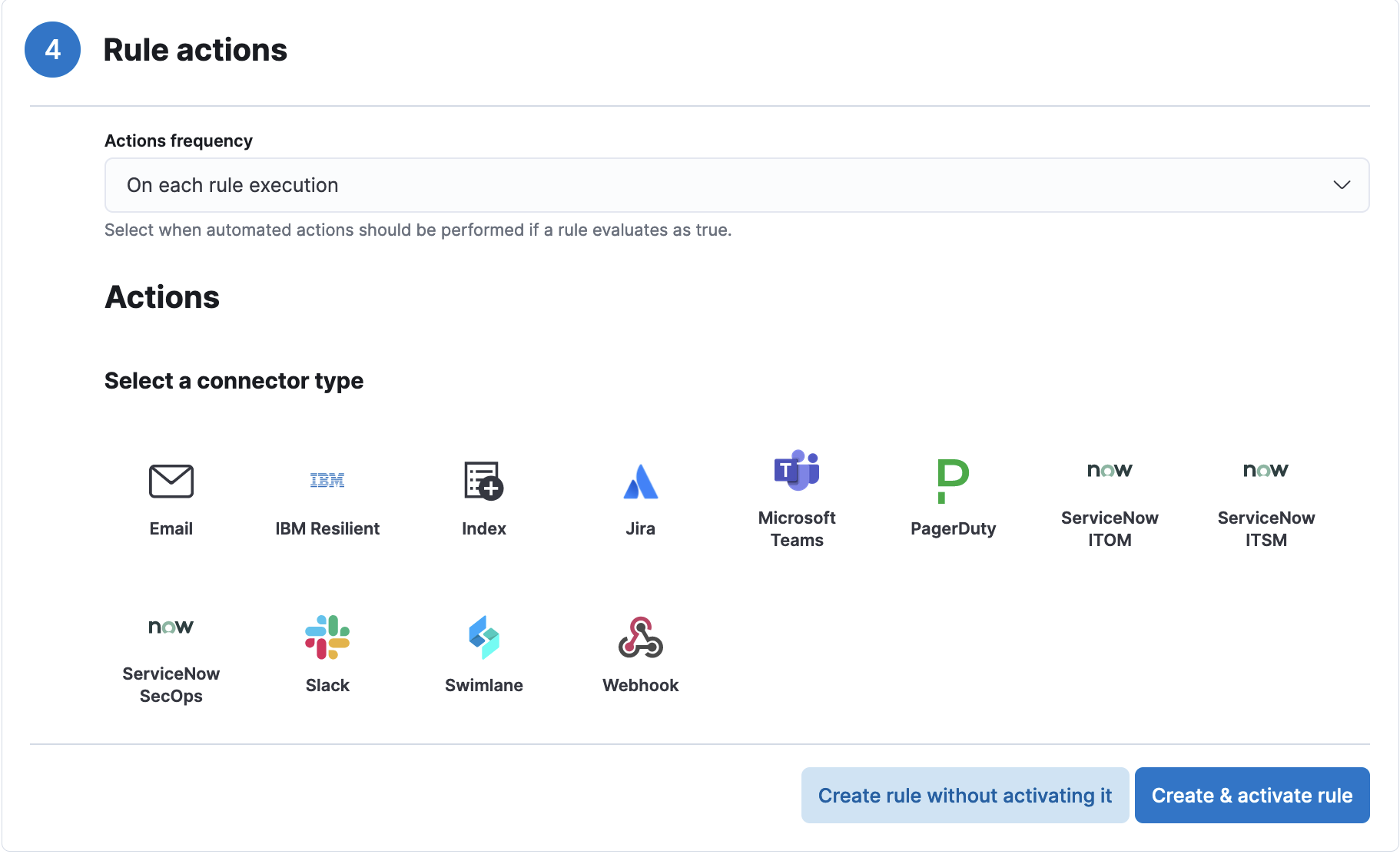
- In the Rule actions section, set Actions frequency to "On each rule execution." This will ensure that the alert is triggered each time the behavior is detected.
- Under Actions, selected a connector type of your choice and enter the corresponding details. Make sure at least one connector is selected, so that an alert will be sent out upon detection.
Optional Extra Step
If you would like to also detect Microsoft Diagnostic Tool execution from File Explorer, repeat the above steps with the following EQL query. Please keep in mind that this query is more likely to result in false positives, as the Diagnostic Tool process can be spawned from File Explorer in normal situations unrelated to the exploit.
process where event.type in ("start", "process_created") and
(process.pe.original_file_name : "msdt.exe" or process.name : "msdt.exe") and
(process.parent.pe.original_file_name : ("explorer.exe") or
process.parent.name : ("explorer.exe"))