Overview
Expedient offers clients 2-factor authentication (2FA) to Expedient Secure User VPN with OneLogin as an identity provider. If preferred, a client can substitute OneLogin for a different SAML identity provider and 2FA solution that their users may already utilize to access other applications. Examples of alternative identity providers and 2FA solutions include Azure AD, Duo, and Okta. While Expedient may not manage these alternative solutions, Expedient is providing this documentation to assist clients with getting started with integrating their 2FA solution with Expedient Secure User VPN. If a client chooses to use a non-Expedient managed identity provider, it is the client's responsibility to manage that solution. This document outlines the process for securing Expedient Secure User VPN with Duo Single Sign-On.
Prerequisites
The steps described in this document assume that the client has already configured Duo Single Sign-On with Active Directory as its Authentication source.
This document assumes that you have already configured an MFA policy for your users within Duo that requires them to use the Duo.
Please refer to the Duo website for the subscription levels that support securing applications via SAML.
Process
Integrating an identity provider with Expedient Secure User VPN, backed by Palo Alto Networks Global Protect, follows the same outline regardless of vendor.
Access identify provider configuration, create Palo Alto Global Protect application, provide VPN domain name, and get authentication attributes.
Navigate to firewall UI after successfully authenticating into fw.expedient.cloud.
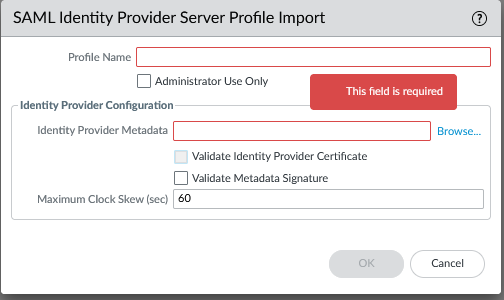
Create a SAML identity provider server profile utilizing the attributes gathered.
Device > Server Profiles > SAML Identity Provider > Import
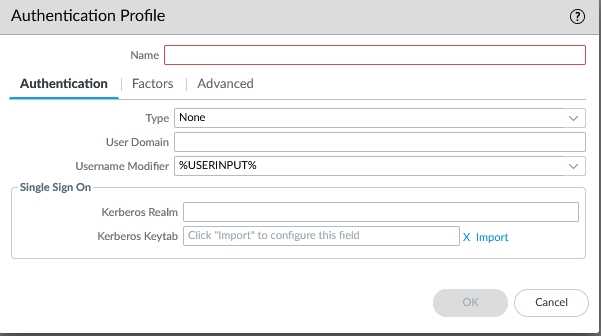
Create authentication profile utilizing server profile created.
Device > Authentication Profile > +Add
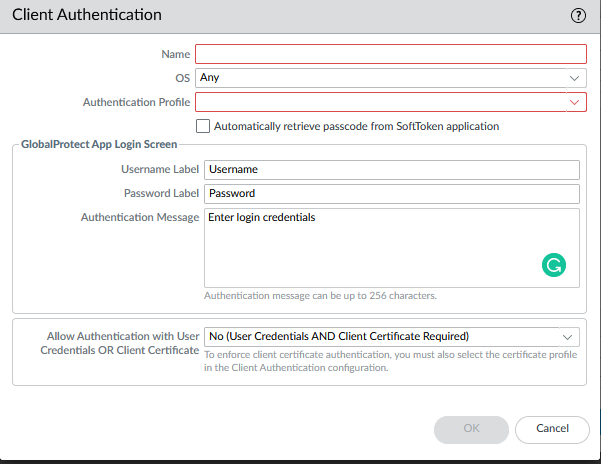
Access global protect portal & gateway configuration tabs and create client profiles pointing to the authentication profile.
Network > GlobalProtect > Portals > Select Portal > Authentication > Client Authentication > +Add
Network > GlobalProtect > Gateways > Select Gateway > Authentication > Client Authentication > +Add
Perform a firewall commit operation.
Please refer to the following Duo document for additional help configuring Duo as an identity provider for Expedient Secure User VPN.
Configure Duo as an Identity Provider for Expedient Secure User VPN