Introduction
You can join a Cohesity cluster to client domains to allow for SMB share authentication and other functionality.
Prerequisites
- Identify a Domain Controller they wish to act as Preferred for AD authentication
- 2 Preferred DCs are highly encouraged but not required
- IP and FQDN are needed from the tenant
- This information is critical, as if we do not set Preferred Domain Controllers, Cohesity will leverage what DNS returns in a round-robin fashion
- If some of those DCs are inaccessible, this will cause intermittent or constant authentication issues
- A network path to the domain controllers from their dedicated Cohesity network must exist
- The client must come equipped with an account and credentials with permissions to join Computer Objects (Domain Administrator) to their domain
- Cohesity SMB functionality utilizes the Kerberos authentication protocol
- Kerberos authentication is much more strict than basic NTLM authentication
- Kerberos functions by the client machine holding an authentication ticket and presenting it to the Cohesity cluster
- You must join any accessing client machine to the same domain you are joining the cluster to and be able to communicate with a domain controller in the domain
- Unjoined machines or machines from a different domain will be unable to receive a Kerberos ticket from said domain
- Linux machines may need additional packages installed to support Kerberos authentication
Network/Port Requirements
Incoming Traffic
Source | Destination | Destination Port | Protocol | Usage Notes | Type of Traffic |
|---|---|---|---|---|---|
Client | Cohesity cluster | 53 | TCP/UDP | Serve DNS requests from an external source. | Management |
Cohesity cluster | Active Directory | 445 | TCP | Required only when initially joining the Cluster to Active Directory. |
Outgoing Traffic
Source | Destination | Destination Port | Protocol | Usage Notes | Type of Traffic |
|---|---|---|---|---|---|
Cohesity cluster | Kerberos Key Distribution Center (AD) | 88 | TCP/UDP | Required for Kerberos if the cluster is configured to use Active Directory. | Management |
| LDAP | 389 | Required if the cluster is configured to use Active Directory or LDAP. | |||
| Active Directory | 137 | TCP | Required only when initially joining the Cluster to Active Directory. | ||
| 139 | Required only when initially joining the Cluster to Active Directory (for the NetBIOS session service). |
Cohesity Static Routing
Depending on the network configuration, the Cohesity cluster may require static routes to complete the network path between the Cohesity cluster and domain controller(s). Adding static routes to the Cohesity cluster is done via the CLI and is the sole responsibility of Expedient. Please reach out to Expedient with the following information:
- IP addresses of domain controllers. Expedient can allowlist a /24, if needed.
- IP addresses/VLAN ID of dedicated the Cohesity node/VIP network.
- Multiple routes may be required if you wish to establish connectivity to multiple servers/networks.
Join the Cluster to the Domain
- Log in to the respective Cohesity Cluster via the GUI
- From the navigation bar at the top of the page, select the Settings → Access Management → Active Directory tab
- Select Add Active Directory
- Enter the applicable information on the Join Active Directory page:
- Domain Name: Domain the client has requested to join
- Username: Account with Domain Administrator access
- Password: Password for the above account
- Preferred Domain Controllers: Set Preferred Domain Controllers to minimize DNS round-robin
- Machine Accounts: Create and match the Machine Account name present within the AD domain
- Mapped Provider: Can be left at the default of None
- OU: Can be left default (optional)
- NetBIOS Name: NETBIOS name of AD instance being joined to (optional)
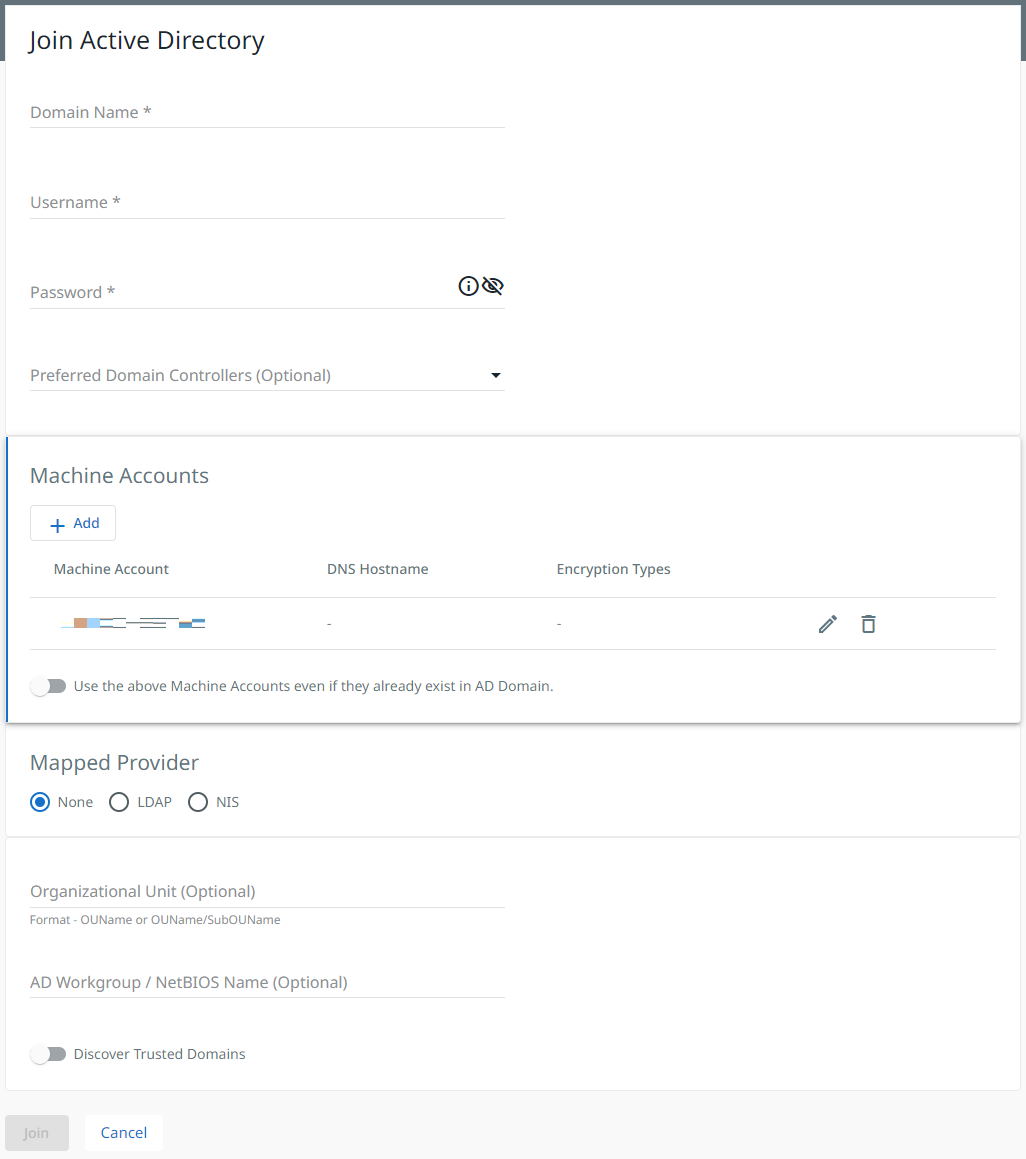
- Select Join after all required fields are filled in.