Active Directory Connector manages IDM user authentication against Active Directory and provide real-time synchronization.
See Installing the Active Directory Connector if you haven't already!
Verify Active Directory connection
Go to Users > Directories and select the directory.
Verify that the Active Directory Connector instance is successfully connected.
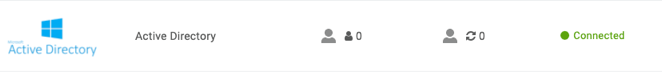
The first number is the total users whose authentication source is set to this ADC instance.
Map and sync Active Directory attributes
To review and update directory attribute mappings, go to the Directory Attributes tab.
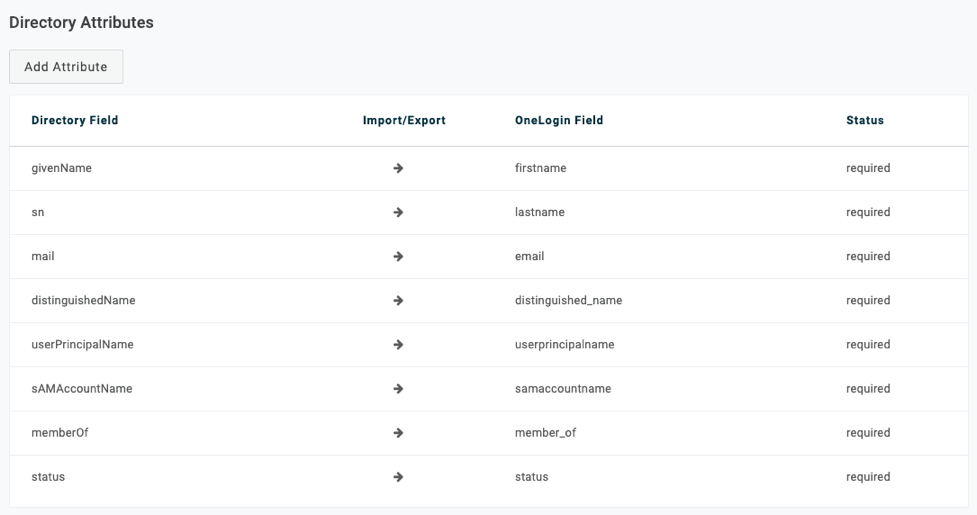
OneLogin also syncs the following fields from Active Directory:
| Active Directory Field | IDM |
| company | Company |
| department | Department |
| manager | Manager |
| manager's objectGUID | manager_guid |
| objectGUID | Object GUID |
| title | Title |
Select Organizational Units to sync from Active Directory
Go to the OU Selection tab to select the AD organizational units to import
The tab displays your domain's DN in the format DC=company, DC=com.
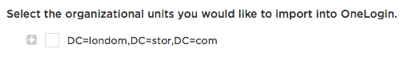
Select the plus button to expand the tree. Initially, only the top level node is displayed. After you select OUs and save, the tree expands to display only the branches and nodes that include selected OUs. To view child nodes, click the plus button to expand the node. To view sibling nodes, click the ellipsis button.
Set advanced Active Directory Connector settings
Go to the Advanced tab to set granular Active Directory Connector settings.
Mappings: Toggle to enable OneLogin to assign OneLogin role and group membership, among other user attributes, based on user membership in AD security groups.
Stage users: Toggle on to move Active Directory users to OneLogin's staging environment (requiring manual approval of users) during sync.
- Turn it off to convert synced AD users automatically to active OneLogin users, without approval steps.
- If this option is on, imported users are listed as Unapproved in Users > Users.
- You can activate users individually on the user detail page, or approve the unapproved users by clicking More Actions and select Approve all users from the drop-down menu.
Sync User Status from Active Directory: Select to ensure users disabled in AD are disabled in OneLogin. This deprovisions users from apps.
Enable Smart Password: Select if you migrate an LDAP directory to this Active Directory instance. This setting also captures user LDAP passwords in Active Directory without requiring a password reset.
Enable auto-switch sync failover: Select if multiple Active Directory Connectors are configured for this Active Directory instance and you want to fail over automatically to another Active Directory Connector if the Active Directory Connector responsible for synchronization fails.
Login username attribute: Select the attribute to map to the username attribute. The username attribute is used to match the user and prevent duplicates. The default value is email address. Users can log in with samAccountName or Email regardless of which field is selected to match to the username attribute.
Exporting users: Select to export user attributes from OneLogin to Active Directory. To export user attributes to AD, switch the sync direction for each attribute on the Directory Attributes tab.
Deleted users in AD...: Select an what action occurs when users are deleted in Active Directory or when a user is removed from scope (for example, removed from an OU set to synchronize with OneLogin):
- unaffected in OneLogin
- suspended in OneLogin (users are set to Inactive but their user record remains)
- deleted in OneLogin (user record is completely deleted from OneLogin directory)
Account owners aren't suspended or deleted regardless of what action is selected. Account owners can be prevented from logging if authenticated by Active Directory and the AD account was deleted. For this reason, Account Owner accounts shouldn't authenticated against external directories like Active Directory.
Enforce OneLogin password expiration policies: Enable Active Directory to maintain OneLogin's policy-based password expiration settings, if the OneLogin policy is more restrictive. If this setting is enabled, the most restrictive password policy is applied: if OneLogin's password expiration interval is less than Active Directory's interval, then the OneLogin setting is applied.
Do not write user status back to Active Directory: If checked then OneLogin doesn't write back user status to Active Directory. If this is checked, the admin can unlock users in OneLogin, regardless of the user status in Active Directory or if OneLogin can change the user status in Active Directory.
Further Reference
KB Article: Automated AD Connector Notifications
External Site: OneLogin Knowledge Base