These steps outline defining a new detection rule for Elastic Security.
Rules are:
based on a list of parameters
targeted at collected data
ran periodically based on a user-defined schedule
can optionally take an automated action when triggered.
For additional details, please see Elastic's official documentation on this topic.
Process
Login to Elastic Endpoint Security. Please refer to How to access Elastic Endpoint Security if you need assistance.
Once logged in, you can begin the process of creating a new rule by navigating to Detect → Rules → Create new rule
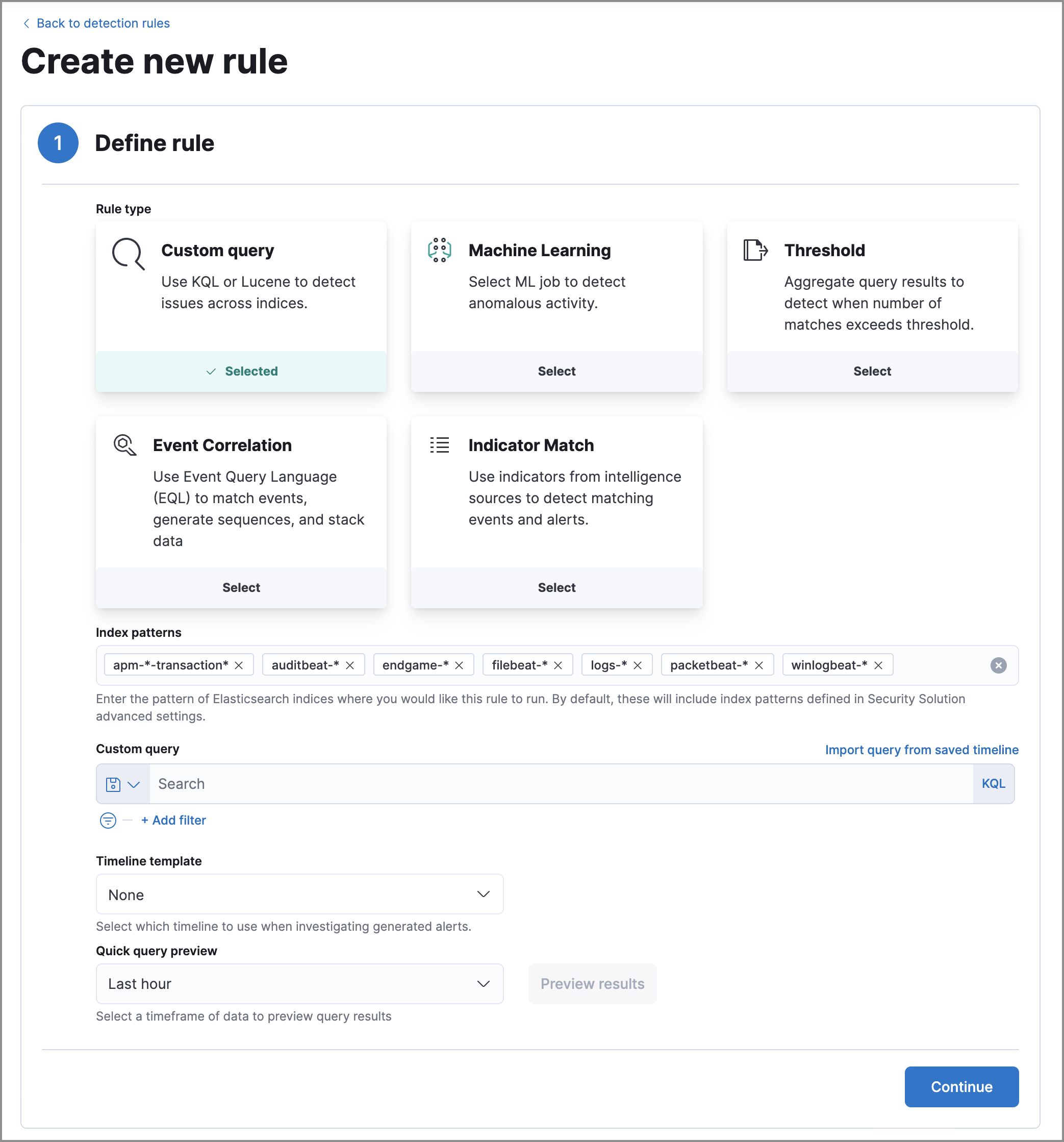
From here, you can select the type of rule you'd like to create and fill in the necessary details to describe the desired behavior. You can find specific information on each type of rule and required parameters in Elastic's detection rule documentation.
The custom query option allows you to import a query from a previously saved timeline, helpful in situations where a security issue has been identified and you are interested in detecting similar behavior moving forward.
Before clicking continue, make sure to perform a query preview with the Preview results button-- doing so will allow you to see the alert volume of the proposed rule. Suppose you find that the query you've defined is particularly noisy. In that case, you may want to consider adding additional conditions to narrow the results and cut down on alert volume.
After defining the rule, you can adjust the rule's schedule and select a connector and action to be performed by Kibana when the alert triggers.