Introduction
To add an EC2 server to a protection job for backups with Cloud Snapshot Manager, you must register the Azure Subscription as a Cloud source within the Cloud Data Protection platform.
Limitations and Considerations
- Cloning is not supported.
- App consistent (quiesced) backups are not supported
- File download is not supported
Permissions
Create an IAM User and assign it a policy with the permissions given in the following example:
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"ec2:AttachVolume",
"ec2:CopySnapshot",
"ec2:CreateSnapshot",
"ec2:CreateTags",
"ec2:CreateVolume",
"ec2:DeleteSnapshot",
"ec2:DeleteVolume",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeInstanceAttribute",
"ec2:DescribeInstanceCreditSpecifications",
"ec2:DescribeInstanceStatus",
"ec2:DescribeInstances",
"ec2:DescribeKeyPairs",
"ec2:DescribeRegions",
"ec2:DescribeImages",
"ec2:DeregisterImage",
"ec2:DescribeReservedInstances",
"ec2:DescribeReservedInstancesListings",
"ec2:DescribeReservedInstancesModifications",
"ec2:DescribeReservedInstancesOfferings",
"ec2:DescribeSecurityGroupReferences",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSnapshots",
"ec2:DescribeSubnets",
"ec2:DescribeVolumeAttribute",
"ec2:DescribeVolumeStatus",
"ec2:DescribeVolumes",
"ec2:DescribeVpcAttribute",
"ec2:DescribeVpcClassicLink",
"ec2:DescribeVpcClassicLinkDnsSupport",
"ec2:DescribeVpcEndpointConnectionNotifications",
"ec2:DescribeVpcEndpointConnections",
"ec2:DescribeVpcEndpointServiceConfigurations",
"ec2:DescribeVpcEndpointServicePermissions",
"ec2:DescribeVpcEndpointServices",
"ec2:DescribeVpcEndpoints",
"ec2:DescribeVpcPeeringConnections",
"ec2:DescribeVpcs",
"ec2:DetachVolume",
"ec2:ModifySnapshotAttribute",
"ec2:RegisterImage",
"ec2:RunInstances",
"ec2:StartInstances",
"ec2:StopInstances",
"iam:AddRoleToInstanceProfile",
"iam:GetAccessKeyLastUsed",
"iam:GetInstanceProfile",
"iam:GetUser",
"iam:GetUserPolicy",
"iam:ListAccessKeys",
"iam:PassRole",
"kms:CreateGrant",
"kms:Decrypt",
"kms:DescribeKey",
"kms:Encrypt",
"kms:GenerateDataKey",
"kms:ListAliases",
"kms:ReEncryptFrom",
"kms:ReEncryptTo"
],
"Resource": "*",
"Effect": "Allow",
"Sid": "VisualEditor0"
}
]
}
Procedure
- Log in to the respective Cloud Data Protection system.
- You should be directed to the Protection Jobs page upon logging into the cluster.
- To register your AWS IAM User as a Cloud Source, select the Data Protection Sources tab from the navigation bar on the left-hand side of the page.

- Click Register | Virtual Machines.
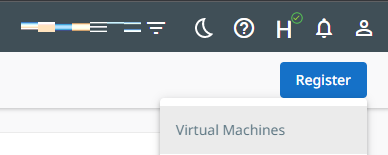
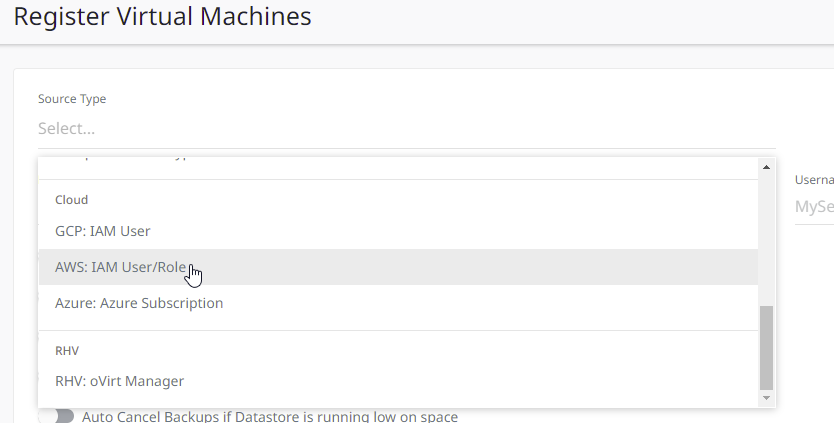
- Under Select Source Type, select Azure: Azure Subscription.
- Select the Subscription Category and enter the Access Key and Secret Access Key of the IAM User, then enter the ARN String associated with your Instance ID (Syntax: arn:aws:ec2:[REGION]:[ACCOUNT ID]:instance/[INSTANCE ID] ). For more information on finding your ARN, see https://docs.aws.amazon.com/general/latest/gr/aws-arns-and-namespaces.html
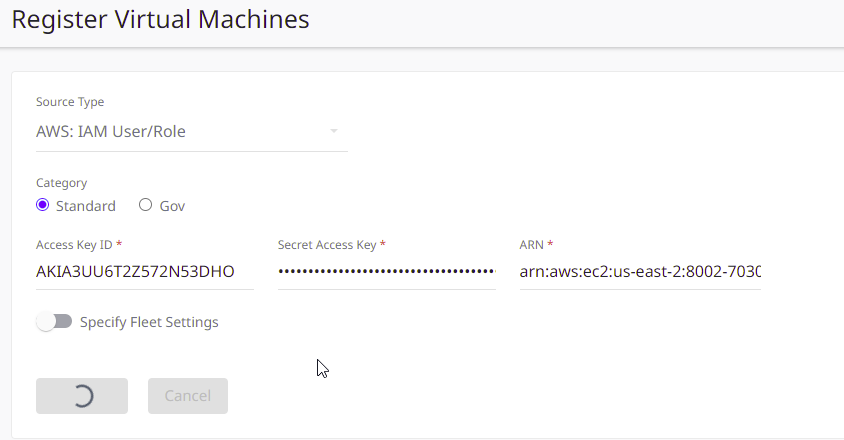
- Click Register.
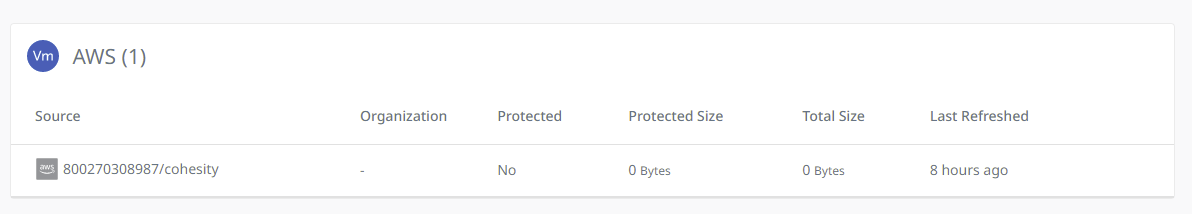
- Confirm the newly registered Azure Source on the Source page.